Technical documentation. Explanatory note to the technical project Explanatory note to the technical specification example
The main purpose of the Explanatory Note document is to provide general information about the system and justification for technical decisions made during its development. Therefore, the basis for the development of the Explanatory Note will mainly be the Terms of Reference.
The explanatory note is one of the most important documents of the technical project. The technical design is developed with the aim of identifying final technical solutions that provide a complete picture of the product design.
When developing a program for creating an explanatory note, it is recommended to use GOST 19.404-79 “Explanatory note. Requirements for content and design."
To create an explanatory note for a technical project describing an automated system (AS), it is recommended to use the standard RD 50-34.698-90 “Automated systems. Requirements for the content of documents".
Many sections of the above documents overlap, so as an example we will consider the document Explanatory Note created on the basis of RD 50-34.698-90
1. General Provisions
1.1 Name of the designed speaker
This section of the Explanatory Note document contains the full and short name of the AS.
For example: “In this document, the system being created is called the Corporate Information Portal. It is also allowed to use the abbreviated name “KIP” or “System.”
1.2 Documents on the basis of which the system is designed
This section of the Explanatory Note document should contain references to the contract and Terms of Reference for the development of an automated system.
1.3 Organizations involved in system development
This section of the Explanatory Note document indicates the names of the customer and developer organizations.
1.4 Goals of AS development
In this section of the Explanatory Note document, the technical, economic and production benefits that the customer will receive after implementing the developed system should be indicated.
For example: “The purpose of the system being created is:
- optimization of the company's document flow;
- support of the company’s corporate culture;
- optimization of communications between company employees. »
1.5 Purpose and scope of use of the developed speaker system
This section of the Explanatory Note document must include a description of the type of activity being automated and a listing of the processes for which the system is intended to automate.
For example: “KIP is designed to provide complete and timely information, as well as effective organization of employee work. The system should ensure the organization of joint work of employees using the following capabilities:
- Creation of conferences to discuss issues;
- Sending/Receiving electronic mail messages;
- Ensuring collaboration on documents;
- Coordination of documents;
- Maintaining records of incoming and outgoing documentation.”
1.6 Information about the regulatory and technical documents used in the design
This section should indicate the standards that were used to create the Explanatory Note document.
For example: “The following regulatory and technical documents were used during the design:
- GOST 34.201-89 “Information technology. Set of standards for automated systems. Types, completeness and designations of documents when creating automated systems";
- GOST 34.602-89 “Information technology. Set of standards for automated systems. Technical specifications for the creation of an automated system";
- GOST 34.003-90 “Information technology. Set of standards for automated systems. Automated systems. Terms and Definitions";
- GOST 34.601-90 “Information technology. Set of standards for automated systems. Automated systems. Stages of creation";
- RD 50-682-89 “Methodological instructions. Information technology. A set of standards and guidelines for automated systems. General provisions";
- RD 50-680-88 “Methodological instructions. Automated systems. Basic provisions";
- RD 50-34.698-90 “Methodological instructions. Information technology. A set of standards and guidelines for automated systems. Automated systems. Requirements for the content of documents."
1.7. System creation sequence
For systems created in several iterations, the Explanatory Note should indicate the amount of work for each iteration. Separately, it is necessary to highlight the work planned for this iteration.
For example: “The implementation of the Corporate Information Portal project is planned in two stages.
The first stage of the instrumentation includes the organization of joint work of company employees due to the introduction of such capabilities as:
- Instant messaging;
- Organization of the conference;
- Sending/receiving email;
- Coordination of documents using the System.”
2 Description of the activity process
This section of the Explanatory Note document should reflect the processes and functions automated by the system throughout the entire business process.
To illustrate the material in the explanatory note, it is allowed to use UML, ARIS or IDF0 notations, as well as schematic images created using standard applications (Visio).
To understand the relationship between automated and non-automated functions in the Explanatory Note document, it is necessary to clearly distinguish between user actions and system actions.
For example: “1. The user creates a document
- The user initiates the process of submitting a document for approval
- The system changes the status of the document to “for approval”. »
- Main technical solutions
2.1. Decisions on the structure of the system and subsystems.
This section of the document Explanatory Note provides solutions on the functional structure of the system and its subsystems.
2.2. Means and methods of interaction between system components. Interconnection with external systems
In this section of the Explanatory Note document, it is necessary to indicate a list of systems with which the created product must interact. When describing the interaction of system components in the Explanatory Note, it is necessary to indicate the data exchange format.
For example: “As part of the interaction of instrumentation and external systems, the following technologies are used:
- “Enterprise accounting” - file exchange in the established XML / Excel format.”
2.3. Decisions on operating modes
This section of the Explanatory Note document includes a list and description of the system’s operating modes. Usually the following modes are distinguished: normal mode, test operation mode, service mode. The explanatory note must provide a description of both the regime itself and the cases in which it is introduced.
2.4. Decisions on the number, qualifications and functions of NPP personnel
This section of the document Explanatory Note regulates the activities of maintenance and functional personnel. The explanatory note must indicate the category of employees that belongs to a particular type of personnel and describe their functions within the framework of the system.
For example: “The portal administrator is responsible for:
- database and software integrity;
- preventive measures to ensure data safety;
- distribution of access rights and registration of users in the system. »
2.5. Ensuring the consumer characteristics of the system specified in the technical specifications
This section of the Explanatory Note document is created on the basis of the product quality requirements specified in the technical specifications. Here it is necessary to describe the parameter by which the quality of the system is determined. The explanatory note also indicates the solutions by which this characteristic was achieved in the system.
For example: “Fault tolerance and operability of instrumentation software modules is ensured through the use of industrial software platforms IBM WebSphere Portal, Enterprise Oracle 10g.”
2.6. Composition of functions and set of tasks implemented by the system
This section of the Explanatory Note document contains a list of tasks that the system solves. In the explanatory note, functions and a set of tasks can be presented in the form of an unnumbered list.
2.7. Decisions on a set of technical equipment and its placement at the site
This section of the Explanatory Note document contains decisions on the technical architecture of the system and requirements for the set of technical means necessary to ensure its correct functioning.
It is recommended to place the requirements for a set of technical means in the explanatory note in the form of a table.
For example: "
|
Equipment |
Technical specifications |
|
Database Server |
|
|
Rack mount version |
No more than 4U |
|
Processor architecture |
RISC (64-bit) |
|
CPU frequency |
at least 1.5 GHz |
|
CPU cache |
At least 1MB |
|
OS |
Windows 2003 SP2 |
|
Possible number of installed processors |
At least 4 |
|
Number of installed processors |
|
|
Possible RAM capacity |
32 GB with ECC |
|
RAM capacity |
Minimum 8 GB |
|
Availability of interfaces |
10/100/1000 Base-T Ethernet interfaces 2 pcs.; |
|
Video card: |
At least 8MB. |
|
Possible number of installed hard drives |
At least 4 |
|
Number of installed disks |
|
|
Reader |
|
|
Power supply |
Input parameters: |
»
When describing the placement of objects of a complex of technical means in the explanatory note, it is necessary to be guided by the requirements of SNiP 11-2-80 for buildings of category "B".
2.8. Volume, composition, methods of organization, sequence of information processing
Information support includes in-machine and extra-machine information support. The internal information support is provided by the Database (DB), input and output documents coming from external systems.
The off-machine information base is formed by data contained in paper documents. Often, when developing automated systems, only an in-machine information base is used, so the main emphasis in the Explanatory Note document should be on the content of this section.
When describing the internal information base in the Explanatory Note document, it is necessary to indicate input and output documents and messages for all subsystems and external systems.
For example: “The input information for the electronic document management subsystem is:
- electronic versions of production workflow documents;
- electronic digital signature;
The output information for the electronic document management subsystem is:
- document life cycle history log;
- document approval history log;
- file of the electronic version of the document in RTF format. »
2.9. Composition of software products, operating languages, algorithms of procedures and operations and methods of their implementation
This section of the Explanatory Note document should contain the technologies and means for developing the system.
For example:
«
- Database server: Oracle 10g
- Portal: Websphere Portal Extend v6.0.
- Business Modeling: ARIS
»
3 Measures to prepare the automation object for putting the system into operation
This section of the Explanatory Note document describes the following activities:
- measures to bring information into a form suitable for computer processing;
- activities for training and testing the qualifications of personnel;
- measures to create the necessary units and jobs;
- measures to change the automation object;
- other activities based on the specific features of the systems being created
27.10.2016 09:57:23
This article discusses the technical project stage, which relates to one of the stages of the information security system (ISS) life cycle - the “design” stage, which, in accordance with the domestic standard GOST 34.601-90, immediately follows the development of the Terms of Reference for the information security system.
1. Development of technical design documentation for NIB
The life cycle of an information security system (hereinafter referred to as ISS) in general consists of the following stages:
- analysis of requirements for information security systems;
- design;
- implementation;
- implementation;
- exploitation.
This article discusses the stage of the technical project, which belongs to the “design” stage and, in accordance with the domestic standard GOST 34.601-90, immediately follows the development of the Terms of Reference for the information security system.
1.1. Why develop documentation for NIB at all?
The answer to this question should be considered in two planes: in the plane of the owner of information resources (for the protection of which an information security system is created) and in the plane of the direct developer of the information security system.
For the owner of information resources, it is important to obtain the result in the form of a functioning information security system that reduces the risks of compromising restricted access information in the organization. The technical project in this case serves to develop the fundamental principles of the future system, namely, it includes a description of how the ISS will be built and function, what measures and means will ensure information protection, what are the possibilities for developing and improving the system. Upon completion of the development of a technical project for an information security system, the Customer receives a comprehensive set of documentation for the information security system, describing all the technical nuances of the future system.
For the direct executor, at the stage of the technical project, it is necessary to lay down the most suitable ISS architecture, as well as make the right choice of measures and means of protecting information in the organization. It is also important to ensure that the characteristics and properties of the system comply with the technical specifications, or to justify, with the participation and consent of the Customer, the adjustment of the requirements specified in the technical specifications in order to increase the efficiency of the system being created.
Thus, as a result of the development of technical design documentation, the Customer will have answers to the following questions:
- what is the general architecture of the NIB;
- what measures and means will be used to implement information protection requirements;
- how the NIB will function;
- what changes in the organization necessary to increase the level of information security will follow as a result of the implementation of the ISS;
- will the Customer's requirements (business requirements) and the requirements of regulatory legal acts in the field of information security be taken into account when developing and implementing the information security system and, if so, how.
In the process of developing technical project documentation, the contractor will receive the following results:
- a basis for the transition to the next stages of building an ISS, namely the stages of working documentation and implementation;
- understanding of the architecture, technologies and tools used, the order of building the system;
- how the Customer’s requirements (business requirements) and regulatory documents in the field of information security are implemented for the system.
1.2. Review of approaches to developing technical project documentation
The development of a technical project for an information security system is most often carried out on the basis of relevant standards and guidance documents. Moreover, their use is mandatory for government institutions, but recommended for commercial ones. In practice, commercial organizations also use state standards when developing technical project documentation for the following reasons:
- a repeatedly tested approach to creating information systems;
- thoughtful structure and content of documents;
- a set of documents sufficient for the development and description of almost any system.
To develop documentation for the technical project (TP) stage of the NIB, state standards and guidance documents of the 34 series are used:
- GOST 34.201-89 “Types, completeness and designation of documents when creating automated systems.” This standard specifies:
- types and names of documents at the TP stage;
- completeness of documentation;
- accepted document designations;
- rules for designating NIB and their parts.
- GOST 34.003-90 “Terms and definitions”;
- GOST 34.601-90 “Automated systems. Stages of creation." The standard specifies:
- list of stages of work carried out at the technical stage;
- detailed description of the work carried out at the technical stage;
- list of organizations participating in the creation of the ISS;
- RD 50-34.698-90 “Automated systems. Requirements for the content of documents." This guidance document specifies the requirements for the content of documents at the TC stage.
It is important to understand that according to the 34 series of standards, technical design is a stage of creating a system, and not just a set of documents. In practice, this stage is often combined with the preliminary design stage, which serves to develop several preliminary solutions and justify the most suitable one. Such a combination is allowed by the standard, but it must be taken into account that this does not negate the need to achieve the goals of the preliminary design stage.
Most often, the preliminary design stage is developed in the case when the requirements of the technical specifications for the system can be implemented in several fundamentally different ways, and also when among these methods there are no clearly preferable ones.
However, it is worth noting that the above standards are too general and mainly implement design and general structural functions. To develop the substantive part of the technical project stage documents, designers use information from the following sources:
Current regulatory documents (RLA) regulating the requirements for the protection of certain restricted access information. These regulations present requirements for measures to protect information in information systems, describe the nuances of implementing these measures and additional strengthening measures. Among the current legal acts are the following:
- Order of the FSTEC of Russia dated February 18, 2013 No. 21 “On approval of the composition and content of organizational and technical measures to ensure the security of personal data during their processing in personal data information systems”;
- Order of the FSTEC of Russia dated February 11, 2013 No. 17 “On approval of requirements for the protection of information that does not constitute a state secret contained in state information systems”
- Order of the FSTEC of Russia dated March 14, 2014 No. 31 “On approval of requirements for ensuring information security in automated control systems for production and technological processes at critical facilities, potentially hazardous facilities, as well as facilities that pose an increased danger to the life and health of people and for the natural environment;
- methodological document “Measures for protecting information in state information systems”, approved by the FSTEC of Russia on February 11, 2014.
Requirements for the protection of restricted access information and lists of protective measures vary for information systems of different levels/classes of security. If the information in an organization is not protected in accordance with the federal laws of the Russian Federation (for example, official secrets), then the owner of this information can use the approaches proposed in these regulatory legal acts for building a corporate information security system.
Russian and foreign standards describing various approaches to ways of implementing the stages of the life cycle of building an ISS, including the technical design stage:
- a series of state standards GOST R ISO/IEC 2700X, identical to international standards ISO/IEC 2700X. These standards describe the PDCA (Plan, Do, Check, Act) process approach to the implementation of the life cycle of an information security management system, which is an integral part of the information security system;
- NIST SP 800-64 is a US National Institute of Standards and Technology standard that describes the information systems development life cycle;
- NIST SP 800-37 is a US National Institute of Standards and Technology standard that provides guidance for integrating risk management into the information systems development life cycle.
Manufacturer's operational documentation for information security equipment and auxiliary equipment. These documents contain comprehensive technical information about the tools used in the construction of information security systems, including those directly related to the implementation of information security measures not related to, for example, servers, data storage systems, virtualization tools and others. The general set of such documents varies from manufacturer to manufacturer and depends, among other things, on the implementation of a particular tool (hardware/software). Below is a standard set of operational documentation for information security tools used to develop documents at the technical project stage:
- general description (datasheet);
- administrator's guide (may include local and centralized management guide);
- user guide;
- Quick Installation and Deployment Guide (for hardware information protection systems);
- operator's manual;
- Guidance for deployment in virtual infrastructure (for software information protection systems);
General information about existing SIS architectures, best practices in terms of building ISS, guidelines for security and integration of information security systems with each other, information about problems in the interaction of certain information security systems. Examples of such information may include the following documents:
- guides on information security system architectures, for example: Defense-in-Depth, Cisco SAFE, Check Point SDP and others;
- best practices in the field of information security, for example, available at these links (https://www.sans.org/reading-room/whitepapers/bestprac/, http://csrc.nist.gov/publications/nistpubs/800-14 /800-14.pdf). These documents are most often presented in English, however, any Russian manufacturer of protective equipment has its own best practices for implementing security measures and can provide them upon request;
- security guidelines for information security systems and operating environments. An example is the “Security” section on the official Microsoft portal (https://technet.microsoft.com/ru-ru/library/dd637672.aspx).
1.3. Development of a technical project for NIB in accordance with GOST 34
The development of documents at the technical project stage for ISS is most often carried out by integrators of these services and is implemented mainly in accordance with the following plan:
Determining the list of documents to be developed - this information is indicated in the technical specifications for the ISS. In some cases, the document developer, in agreement with the Customer, may expand or reduce this list, if this possibility is provided for in the technical specifications;
Development of document templates for the TP stage - the structure is used in accordance with RD 50-34.698-90 and GOST 2.106 (for some documents), formatted in accordance with GOST 2.105-95;
Development of the substantive part of documents. Requirements for the system are established in the technical specifications for the NIB. In accordance with these requirements, a list of protective technical and organizational measures required for implementation in the system is determined. Protection measures can be determined in the relevant regulations (depending on the type of information being protected), corporate standards and information security policies, as well as based on the presence of current security threats identified during the development of the organization's threat model. Based on the list of protection measures, the IS developer selects appropriate information security tools and develops the functional structure of the information security system (subsystems, components). Further, the technical design documents describe the practical implementation of protection measures based on the selected security protection or organizational measures in the organization's infrastructure.
Coordination of the developed documentation and the solutions presented in it with the Customer of the system.
When developing technical project documentation, most often it is not necessary to develop a complete list of documents specified in GOST 34.201-89, since this standard is outdated and some of the documents do not take into account the development trends and technologies of modern information systems. The minimum set of documents required to describe the information security system is as follows:
- technical design statement;
- explanatory note to the technical project;
- functional structure diagram;
- structural diagram of a complex of technical means;
- organizational structure diagram;
- list of purchased items.
At the Customer’s request or in the event that the ISS is a complex multi-component system, the following documents can also be additionally developed:
- automation scheme;
- description of automated functions;
- description of the information support of the system;
- description of the complex of technical means;
- software description;
- description of the organizational structure.
It should be noted that GOST 34.201-89 allows for an expansion of the range of documents at the TP stage, but in practice there are more than enough of these documents.
Technical design sheet
Designation: TP.
This document is intended to describe the list of documents developed at the technical project stage. The number of pages of each of the developed documents is also indicated.
Explanatory note to the technical project
Designation: P2.
This document is the main one for the TP stage and includes a description of the ISS architecture, technical and organizational measures, ISS functions, software and hardware systems, and other things. According to the standard, it consists of four main sections:
- general provisions;
- description of the activity process;
- basic technical solutions;
- measures to prepare the automation object for putting the system into operation.
Functional structure diagram
Designation: C2.
This document describes the logical structure of the ISS, namely:
- logical subsystems and components included in the ISS;
- functions implemented by means of subsystems and components;
- information connections between logical elements of the SIS and types of messages during exchange.
Structural diagram of a complex of technical means
Designation: C1.
This document includes a description of the following elements of the ISS:
- technical means as part of logical subsystems and components of information security systems;
- communication channels and exchange between technical means indicating transport protocols.
Organizational chart
Designation: C0.
This document describes the organizational structure of the organization in terms of ISS management, namely:
- divisions and responsible persons of the organization involved in the functioning of the ISS;
- functions performed and connections between departments and responsible persons.
List of purchased items
Designation: VP.
This document includes a list of all software and hardware, as well as licenses used to create an information security system. Developed in accordance with GOST 2.106.
Note. It is also worth noting here that the guiding document RD 50-34.698-90 allows for the addition of any document at the TP stage (the inclusion of sections and information different from those proposed), the merging of sections, as well as the exclusion of some individual sections. Decisions about this are made by the developer of documents at the TP stage and are based on the features of the created NIB.
1.4. Rules for developing documentation
- structural compliance with state standards;
- strict compliance with the requirements of the technical specifications for the system;
- application of document templates (use of uniform styles, markup, fields, etc.);
- an individual approach and the simultaneous use of existing developments when filling out sections of documents.
Explanatory note to the technical project:
- document development is carried out in Microsoft Word; after development is completed, it is recommended to convert the document to PDF format for convenience;
- terms and abbreviations must be consistent throughout all sections of the document;
- It is recommended to avoid obvious repetitions and unnecessary increase in the length of the document;
- technical solutions must be described in as much detail as possible, indicating:
- architecture and technologies used;
- locations of software and hardware in the organization’s infrastructure;
- information security tools used with a description of their characteristics, implemented functions, information about certification;
- basic settings of information security tools in terms of protection mechanisms, addressing, routing, interaction with related systems and tools, etc.;
- controls, methods of access to them and places of their installation;
- diagrams (structural, functional, organizational):
- develop diagrams in Microsoft Visio;
- after development, insert diagrams into the document using the “Paste Special” dialog in EMF format (Windows metafile);
- develop separate diagrams for the system, subsystems and components of subsystems;
- make the design of the diagrams uniform, using the same elements, abbreviations, icons, text styles, etc.
1.5. Resources to help you develop documentation
The Internet contains a huge amount of information that, to one degree or another, can help in the development of technical project documentation. Key resources are presented in the table below.
Table. SIS Technical Design Resources
| Resource type | Information | Examples of resources |
|---|---|---|
| Internet portals of federal executive authorities | Regulatory documents, methodological recommendations, registers (including certified information security systems), databases (including databases of vulnerabilities and threats) | fstec.ru clsz.fsb.ru minsvyaz.ru/ru/ |
| Internet portals of information security manufacturers, distributors of information security solutions | Description of information security solutions, operational documentation for information security, analytical materials and articles | securitycode.ru kaspersky.ru/ drweb.ru/ ptsecurity.ru/ infowatch.ru/ infotecs.ru/ cisco.com/c/ru_ru/index.html checkpoint.com altx-soft.ru |
| Specialized information security resources | Comparison of information security solutions, review articles on information security solutions, tests of information security solutions, in-depth technical information about information security technologies | anti-malware.ru bis-expert.ru safe.cnews.ru securitylab.ru/ vulners.com/ csrc.nist.gov itsecurity.com owasp.org sans.org |
1.6. Examples of technical project stage documents
To understand the requirements for the content of documentation at the TP stage, below are examples of filling out the main documents (sections of documents).
1.6.1. Explanatory note to the technical project
The explanatory note is a fairly voluminous document, so here is an example of the content of the section “Basic technical solutions” in part of one of the SIS subsystems - the security analysis subsystem.
ISS security analysis subsystem
Structure and composition of the subsystem
The security analysis subsystem (SAS) is designed to systematically monitor the security status of automated workstations (AWS) of personnel and organization servers. The basis of the ESD is the “Test” software tool produced by Information Security LLC. SZI Test is certified by FSTEC of Russia for compliance with technical specifications (TU) for information security and for the 4th level of control over the absence of undeclared capabilities.
The ESD includes the following components:
- Test Server management server;
- Test Console management console.
A description of the subsystem components is presented in the table below.
Table. ESD components
| Component | Description |
|---|---|
| Test Server Management Server | Provides management of scanning tasks, performs functions of monitoring the security status of workstations and servers of the organization. Scanning parameters are set by the information security administrator on the Test Server management server. All collected information about scan results is stored in the Test Server server storage based on the Microsoft SQL Server 2008 database management system |
| Test Console | Allows the information security administrator to connect to the Test Server, view and change its configuration, create and modify scanning tasks, view information about the progress of tasks and the results of their execution. The management console is installed on the information security administrator's workstation |
Providing functions
The ESD provides the following functions:
- implementation of proactive protection of the organization's workstations and servers by monitoring the status of information security;
- automation of processes for monitoring compliance with internal policies and certain security standards;
- reduction of costs for auditing and security control, preparation of status reports;
- automation of resource inventory processes, vulnerability management, monitoring compliance with security policies and change control.
Solution for a complex of hardware and software tools
The list of used ESD software and hardware is given in the table below.
Table. ESD software and hardware
ESD control server
Technical means
The physical server used as an ESD management server must meet the technical requirements for the software and OS installed on it, given in the table below.
Table. OS and software requirements for the ESD control server
| Software | Technical requirements | |
|---|---|---|
| CPU | RAM, MB | |
| Microsoft Windows Server 2008 R2 | 3000 MHz, 4 cores | 8192 |
| Microsoft SQL Server 2008 R2 | ||
| Test Server Software | ||
Software
Management server OS
Windows 2008 R2 OS is installed on the management server in the normal manner from a boot distribution.
The management server OS is managed both locally from the console and via the RDP protocol.
Management server DBMS
The Microsoft SQL Server 2008 R2 database is installed under an account with local administrator rights using the standard installation wizard from the distribution kit supplied by the product developer.
Test Server Software
Test Server software is installed on the management server using the standard installation wizard.
The initial setup and subsequent management of Test Server software in normal mode is carried out using the Test Console management console installed on the IS administrator's workstation.
IS administrator's workstation
Technical means
The existing workstation of an employee of the organization's department responsible for providing information security, running the Microsoft Windows family of operating systems, is used as a platform.
The technical means of the information security administrator's workstation must have the following hardware configuration characteristics (at least recommended):
- CPU 2 GHz;
- RAM 4 GB;
- HDD 80 GB.
Software
Test Console software
The information security administrator's workstation on which the Test Console software is installed must operate under one of the following OS:
- Microsoft Windows 7, 32- and 64-bit;
- Microsoft Windows 8/8.1, 32- and 64-bit.
In addition, for the Test Console management console software to work correctly, Microsoft .NET Framework version 3.5 SP1 or higher must be installed on the information security administrator's workstation, and the security settings of the operating system used must allow access to the Test Server.
Installation of Test Console software on the ESD administrator's workstation is carried out using the standard Test Server software installation wizard with the selected option to install the Test Console management console and other default settings.
Interaction with adjacent systems
For ESD, adjacent are:
- firewall subsystem tools;
- Active Directory directory services;
- Workstation and servers of the organization.
To ensure network interaction with adjacent systems and directly between the ESD components themselves, the passage of the necessary network traffic must be organized.
To ensure the ability to receive updates to the knowledge base and Test software modules for the Test Server scanner, it is necessary to provide access to the update.com web server of the Information Security LLC company via port 443/tcp.
When scanning in PenTest mode, interaction between the Test Server scanner and the workstation and the organization's servers is carried out via the IP protocol. When scanning in Audit and Compliance modes, remote management protocols WMI, RPC, etc. are used. To scan hosts on devices with firewall functions, you must allow connections from the Test Server to the scanned hosts via IP. Accordingly, the Test Server must be provided with access to the network ports of the scanned hosts using the appropriate remote control protocols.
Since ESD, when scanning in Audit and Compliance modes, uses remote control protocols for analysis, Test software scanning tools must undergo authentication and authorization on the scanned node. In ESD, to scan nodes in the Audit and Compliance modes, accounts with administrative privileges are used in each type of node (workstation, server, application systems, DBMS, etc.).
All registered information security events are stored in the Microsoft SQL DBMS. These events can be sent to the information security event monitoring subsystem using special connectors.
Operation and maintenance of ESD
Subsystem users
Operation and maintenance of ESD tools is carried out by employees of the organization with the functional role of “IS administrator”.
An information security administrator is defined as a specialist whose tasks include:
- determining the scanning parameters of the organization’s nodes;
- setting up and launching scanning tasks;
- analysis of scan results for the presence of vulnerabilities in information systems, configuration errors or non-compliance with technical standards;
- control over the elimination of vulnerabilities;
- formation of standards and requirements that apply to ensuring the security of workstations and servers of the organization.
System operating modes
Normal operating mode
In normal operation, the ESD operates 24 hours a day, 7 days a week.
In normal operation, the information security administrator performs:
- scheduled and unscheduled scanning of nodes;
- generating reports;
- updating knowledge bases and Test software modules.
Emergency operation
If the performance of the safety equipment is disrupted, the functioning of the subsystem is disrupted. Failure to operate ESD equipment does not affect the functioning of the organization's automated workstations and servers.
1.6.2. Functional structure diagram
Functional diagrams can be developed for the entire information security system or for part of it, for example, a subsystem or component.
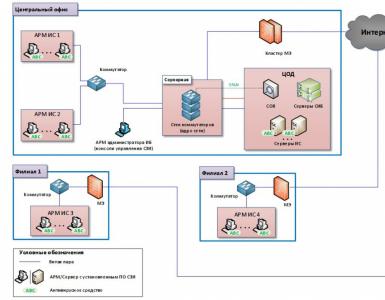
An example of a general functional diagram of an ISS is shown in the figure below.
1.6.3. Structural diagram of a complex of technical means
The block diagram of a complex of technical means can be developed both for the entire ISS and for its parts - subsystems and components. The feasibility of developing diagrams for parts of the information security system is determined by the scale of the system and the required detail.
An example of a block diagram of a complex of technical information and security systems is presented in the figure below.

Ministry of Economic Development and Trade of the Russian Federation
I APPROVED |
||||||||||||||||||||||||||||||||||||||
|
State contract No. 000-05-07 dated October 29, 2007, concluded between the Ministry of Economic Development and Trade of the Russian Federation and CJSC PROGNOZ, to carry out work on the topic “Development of an automated module for federal monitoring of socio-economic development of constituent entities of the Russian Federation within the framework of creating a unified information system for monitoring key indicators of the socio-economic development of the Russian Federation and monitoring the performance of government bodies in achieving them.” When developing this document, the Guiding document on standardization GOST RD 50-34.698-90 was used. 1. General provisions... 5 1.1. Full name of the system... 5 1.2. Documents on the basis of which the design is carried out.. 5 1.3. Stages and deadlines.. 5 1.4. Goals and purpose.. 7 1.5. Compliance of design solutions with safety requirements .. 8 1.6. Regulatory and technical documents... 9 2. Description of the activity process.. 10 2.1. List of tasks... 10 2.2. Main functions performed by the Module... 11 3. Basic technical solutions.. 13 3.1. Module structure, list of subsystems... 13 3.1.1. Subsystem of the Centralized Data Storage. 14 3.1.2. Interface component. 15 3.1.3. Adapter software components. 16 3.6.3. The degree of adaptability to deviations in the parameters of the automation object. 26 3.6.4. Acceptable limits for modernization and development of the system.. 26 3.6.5. Reliability requirements. 27 3.6.6. Security requirement. 27 3.6.7. Requirements for ergonomics and technical aesthetics. 28
|
- general provisions;
- description of the activity;
- basic technical solutions;
- events on
[from clause 2.2.1 RD 50-34.698-90]
General provisions
In the “General Provisions” section they provide:
- design and names of documents, their numbers and date, on the basis of which the NPP design is carried out;
- list of those involved in the system, deadlines;
- goals, purpose and AS;
- confirmation of compliance of design solutions with current standards and fire and explosion safety, etc.;
- information about those used in the design;
- information about the best practices used in the development of the project;
- the order of creation of the system and the volume of each.
[from clause 2.2.2 RD 50-34.698-90]
Description of the activity process
In the section “Description of the activity process” they reflect the composition of the procedures (), taking into account the interrelation and compatibility of processes and activities, form the organization of work in the plant [from clause 2.2.3 RD 50-34.698-90]
Main technical solutions
In the section “Main technical solutions” they give:
- decisions on the structure of the system, means and methods of communication for information exchange between subsystems;
- decisions on the interconnection of the system with related systems and its support;
- solutions for system operation;
- decisions on the number, qualifications and functions, modes of its operation, order of interaction;
- information on ensuring the specified consumer characteristics of the system (subsystems) that define it;
- composition of task complexes () implemented by the system (subsystem);
- decisions on the complex, its placement on;
- decisions on the composition of information, volume, methods, types of computer, and documents, sequence and other components;
- decisions on the composition, languages of activities, procedures and operations and methods of their implementation.
The section provides illustrations of other documents that may be included in accordance with GOST 34.201 [from clause 2.2.4 of RD 50-34.698-90]
Measures to prepare the automation object for putting the system into operation
In the section “Preparatory measures for putting the system into operation” the following is given:
- measures to bring information into a form suitable for;
- activities for training and testing the qualifications of personnel;
- measures to create the necessary units and jobs;
- measures to change the automation object;
- other measures based on the specific features of the systems being created.